Just in Time Permissions & Policy as Code
Does it blend?
What Are Just In Time Permissions?
Just-in-time (JIT) permissions are a security approach that grants users access to a system or data only when needed for a specific task and for the minimum amount of time required. Instead of users having permanent or “standing” privileges, JIT access provides temporary elevated access that is automatically revoked after a predefined time limit, significantly reducing the risk of a security breach from compromised credentials.
For example, you could interact with a permission management system that might grant a user a role for a few hours, and then automatically remove that role again at the pre-specified time.
If You Have JIT, do You Still Need PaC?
Perhaps surprising no-one, my answer is: Yes! Absolutely.
Policy About Permissions
First, what decides whether the user should even be able to be granted a particular JIT permissions? Policy. What decides how long the permissions should last? Policy. What decides on the environmental factors involved in using the enhanced permissions (for example, whether the user should be on the VPN, or have 2FA). Policy.
Policy With Permissions
So policy will be used to help determine whether a user should be granted a temporary permission. But policy can also govern what the user can do with that enhanced permission. For example, consider a user who must be on a VPN to be granted an enhanced permission, receiving it, and then immediately disconnecting from the VPN. Should they still be able to access the important systems? The user has been granted access to a health-records database, but they should only be allowed to access data for a particular geographical region. The user has been granted permission to order merchandise from a vendor, but there are complex rules about how much can be ordered, and in what configurations. Again, Policy as Code can help enforce these sophisticated business rules.
Audit Trails
Another aspect of Policy as Code is the decision logs. Yes, having a record that a user was granted a particular permission for a particular time period is useful audit/compliance data. But what did they actually do with that permission? What actions did they take? Decision Logging provides a robust and thorough paper trail of what was done, which is much harder if an application is just checking to see if a user has a particular role.
An Integrated Example
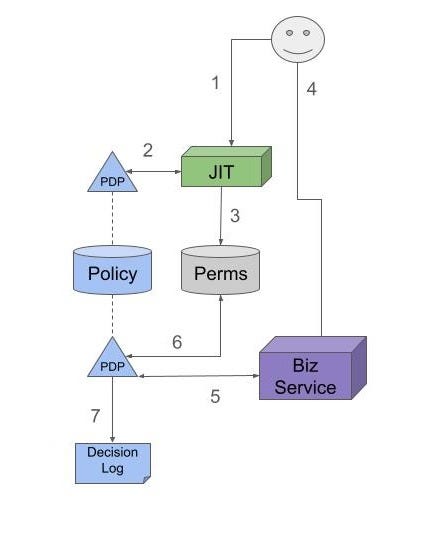
Consider the following diagram:
A user requests for enhanced permissions from a JIT service.
The JIT service verifies the request with a Policy Decision Point (PDP) agent.
The JIT service adds the permission to the Permission data store (which could be Active Directory, LDAP, a database, IAM, etc).
The user accesses the target Service (or application, etc).
The Service verifies the request with a PDP (it could be the same one, or a different one, but they would both generally use the same set of policy rules.
The Policy system can verify with the Permission system that the permission has been granted. Or it could check the claims of a JWT, etc.
The Policy system logs the request and the decision to the decision log, for future compliance audit tracking.
So you can see here that the policy system and the JIT permission system can work quite well together.
Keys for Easy Integration & Future Proofing
If you’re generating lots of temporary permissions, you want to make sure it’s easy for the policy system to learn about those permissions. If the policy solution is slow to take updates, you’ll end up with timing problems.
Whenever you’re about to hard-code regulatory rules or security rules into your application or service, consider using a policy system instead.
Similarly, consider using a policy system to validate the claims in a JWT, and/or to verify the integrity of a certificate. Let the service focus on the business problem, not the security constraints.
JWTs, enhanced with temporary permission already have an expiration date, and require a lot less network traffic to validate.
Summary
Can you use JIT and Policy as Code together? Yes! It’s a great way to handle delegation, emergency escalation and a variety of other common scenarios.
Thoughts? Feedback? Please feel free to comment below or reach out at: johnbr@paclabs.io